Introduction
On Feb. 21, 2025, cryptocurrency exchange Bybit suffered a massive security breach, with hackers stealing roughly $1.4–$1.5 billion worth of crypto assets (reuters.com). Researchers have called it the largest crypto heist in history, noting the haul is more than double the next-biggest crypto theft and possibly “the single largest known theft of any kind”. The stolen funds were primarily Ethereum-based assets from one of Bybit’s wallets.
Approximately 401,000 ETH was drained alongside large amounts of staked Ether derivatives – including about 90,000 Lido stETH and other tokens (e.g., ~15,000 cmETH and 8,000 mETH) – altogether valued around $1.4 billion at the time. Bybit, which serves over 60 million users worldwide, confirmed the incident affected that single Ethereum wallet; other wallets remained secure (reuters.com, coindesk.com). Fortunately, the exchange’s leadership quickly assured clients that no user balances would be lost, as Bybit’s reserves and contingency plans were sufficient to cover the entire amount.

How the Exploit Happened
Bybit revealed that the attack stemmed from a sophisticated exploit of its Ethereum multisig wallet. The breach occurred during what appeared to be a routine transfer from the wallet to a warmer wallet – a process the attackers managed to hijack via malicious tampering (cryptobriefing.com). In an official post, CEO Ben Zhou explained that the wallet’s signing interface had been compromised: the attackers presented the wallet signers with a falsified user interface that showed the correct transaction details and a legitimate Safe (multisig) URL, even as the underlying signing request had been maliciously altered. Tricked by this spoofed interface, Bybit’s signers unknowingly approved a transaction that replaced the wallet’s smart contract logic with a malicious contract, giving the hacker complete control (chainalysis.com).
Subsequent forensic investigations uncovered that the attackers targeted a vulnerability in the third-party multisig wallet provider used by Bybit. The exchange relied on Safe Wallet (formerly Gnosis Safe) for its ETH storage, and North Korean Lazarus hackers reportedly breached Safe’s infrastructure to pull off the heist (bleepingcomputer.com). According to cybersecurity firms Sygnia and Verichains, Lazarus gained access to a Safe developer’s AWS environment and injected malicious JavaScript into the Safe web app frequented by Bybit’s wallet signers (bleepingcomputer.com). That backdoor code remained dormant for most users. Still, it activated when Bybit’s account was detected, allowing the attackers to mask a contract upgrade as a normal transaction and reroute the funds. Notably, Safe confirmed that its smart contracts were never compromised – the exploit was in the web interface delivery – and in response, Safe rolled out a full infrastructure rebuild, credential rotation, and additional transaction verification measures to prevent future exploits.
ByBit’s Response and Remediation
Bybit reacted swiftly once the unauthorized withdrawals were detected. The team publicly acknowledged the breach within hours, with CEO Ben Zhou posting on X (Twitter) that a hacker had “taken control of Bybit’s specific ETH wallet and transferred all the ETH” out (coindesk.com). Zhou immediately reassured users that “all other wallets are secure” and that withdrawals were operating normally for customers (coindesk.com). Out of caution, the exchange did temporarily slow withdrawals during the investigation, but normal operations resumed in about 12 hours. “ALL withdrawals have been processed…you can withdraw any amount and experience no delays,” Zhou wrote the night of the incident, apologizing to users and thanking them for their patience. Bybit promised a comprehensive incident report and vowed to keep the community informed as new details emerged.
Critically, Bybit was financially prepared to absorb the loss. Zhou emphasized that “Bybit is solvent” even if the stolen assets were not recovered, assuring that client assets remained 1:1 backed by reserves. Internal calculations and third-party analyses backed this up – for instance, BitMEX Research quickly reviewed Bybit’s publicly disclosed reserves. It concurred the exchange had enough assets to cover the $1+ billion shortfall. To reinforce liquidity, Bybit secured an emergency bridge loan equal to about 80% of the stolen sum within hours of the hack (cryptobriefing.com).
The exchange decided not to repurchase that missing ETH on the open market (avoiding upward price pressure) and instead planned to use its reserve funds and the loan to plug the gap. Bybit’s peers in the industry also stepped up to help. According to on-chain data, Binance and Bitget deposited over 50,000 ETH into Bybit’s wallets as support on Feb. 22. Bitget’s CEO confirmed a 40,000 ETH transfer from their own funds as a goodwill gesture to bolster Bybit’s reserves. Even a private whale account sent 20,000 ETH ($53 million) to Bybit’s wallet to aid recovery efforts. These moves allowed Bybit to fully restore withdrawals for users by the next day and maintain normal operations.
Industry support: Prominent figures like Binance’s Changpeng Zhao and Tron’s Justin Sun quickly offered help on social media, pledging to assist Bybit in tracking the stolen funds and bolstering security. This public show of solidarity underscored a broader crypto-community effort to mitigate the hack’s impact. Other exchanges, such as OKX and KuCoin, announced they were monitoring for any of Bybit’s stolen assets and would freeze funds or wallets associated with the hack. KuCoin’s CEO issued a statement standing “in full support of Bybit” and committed to helping trace and lock down any suspicious assets that might hit their platform (kucoin.com). This collaborative stance across exchanges aimed to corner the hacker with nowhere to cash out quickly.
Internally, Bybit also mobilized a thorough security overhaul. The exchange brought in leading blockchain forensics firms (including Chainalysis and others) and began working hand-in-hand with law enforcement from day one (markets.businessinsider.com).
The exchange offered a 10% reward (up to ~$140 million) for any white-hat hackers or analysts who helped trace and retrieve the stolen assets (markets.businessinsider.com). Tips and intelligence have been pouring in as a result. Bybit also coordinated with stablecoin issuers – for example, Tether’s CTO Paolo Ardoino froze at least 181,000 USDT linked to the hacker’s Ethereum address (markets.businessinsider.com). According to Chainalysis, collaborative efforts by exchanges and law enforcement led to over $40 million in stolen funds being frozen or seized in the immediate aftermath (chainalysis.com).
Bybit’s leadership has made it clear that hunting down the perpetrator and recovering the funds (where possible) is a top priority. Zhou declared a personal “war against Lazarus” (cointelegraph.com).
On-Chain Movements
The on-chain trail began almost as soon as the funds were stolen. It starts at a single attacker-controlled address, the fresh wallet that received the entire $1.4B haul from Bybit’s wallet. From there, the hacker distributed the funds across several thousand addresses.
From the initial address, the hacker first distributed all funds to 42 wallets in large transactions (the first “hop”) and from there to thousands of other addresses in multiple hops. With each hop, the transacted value usually became smaller and smaller. The hacker started transacting with third-party protocols and entities as early as the second hop. It mainly was changing the ETH derivatives back to ETH for deeper liquidity, but first bridges were also used.
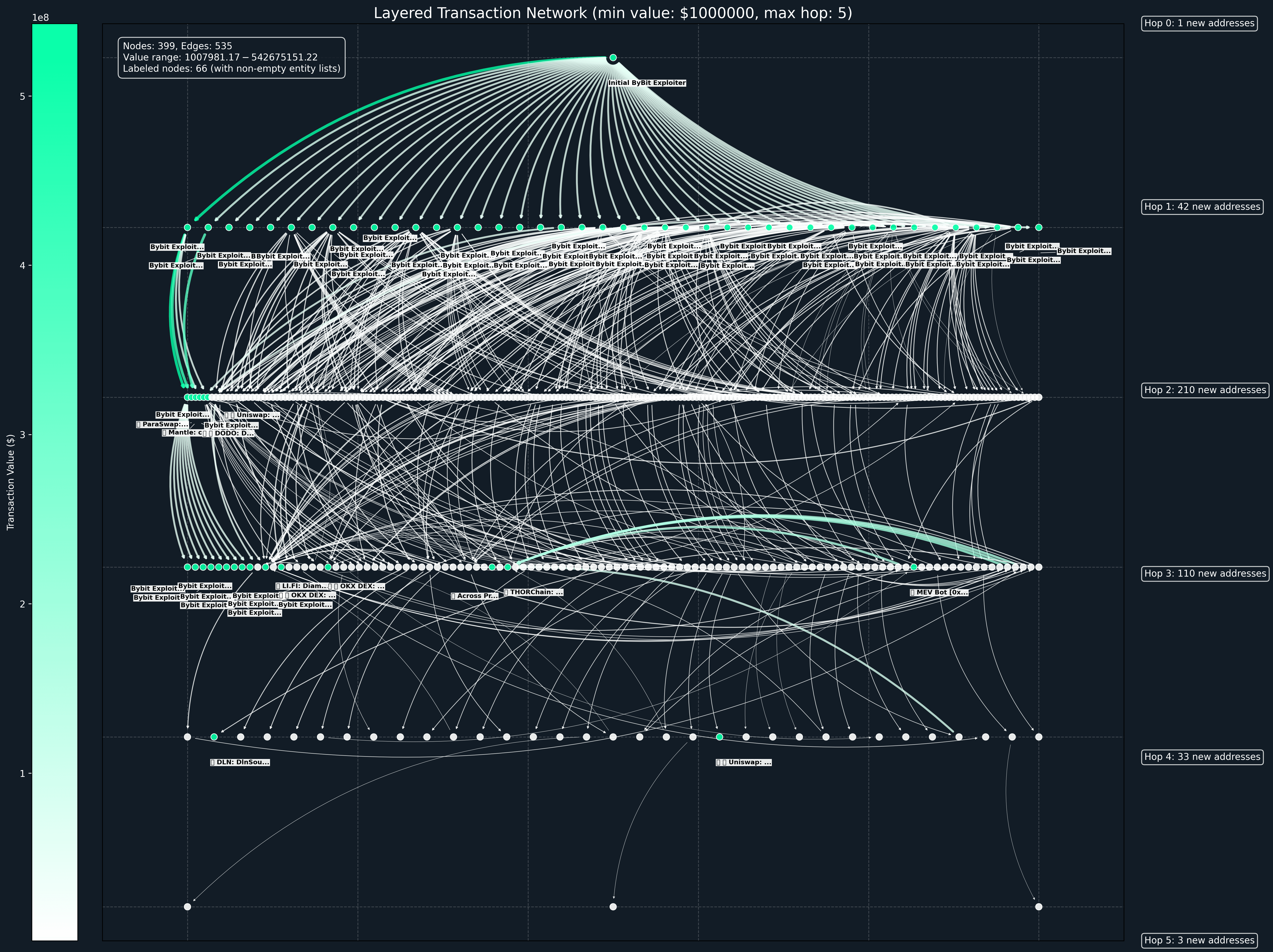
The chart below visualizes flows from the initial ByBit Exploiter trickling down to various addresses for flows of >$1m. The methodology tracked only outflows from wallets, as there were many unconfirmed inflows of various tokens and wallets likely not part of the hack:
- Tracked the outflow volume from the main ByBit hack wallet (excluding inflows due to the number of scam transactions and focus on wallets directly involved in the stolen funds) over the last 14 days.
- Stopped trailing when deposited into contract, or to an entity other than the “ByBit Exploiter” labeled by Nansen.
Zooming in on smaller flows of <$100k, you can see further dispersion, especially in later hops and more varied protocols and entities.
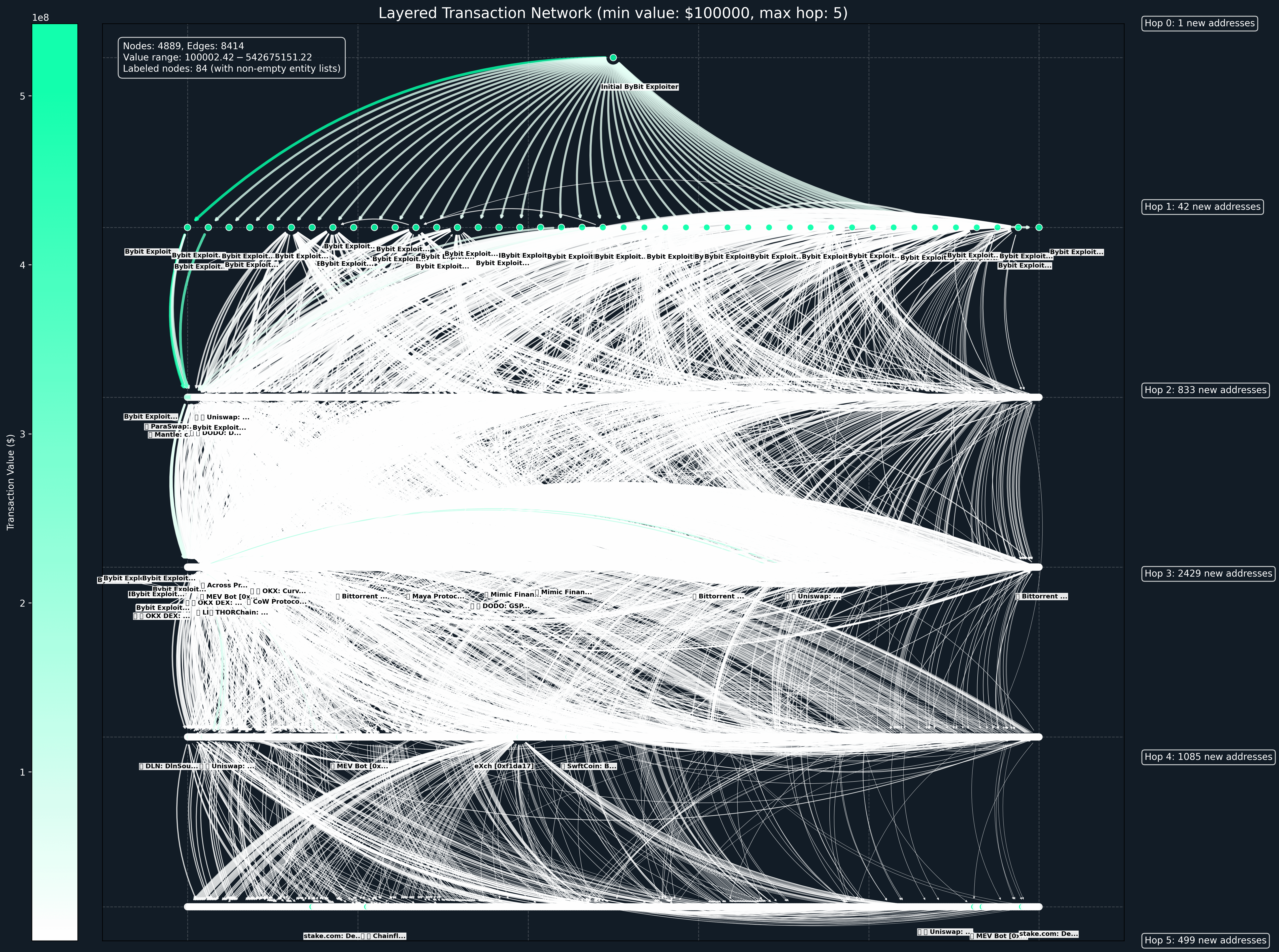
Top interacted entities
Among the entities with the most significant inflows from hacker addresses are THORChain, Paraswap Mantle, OKX DEX, DODO, Uniswap, LI.FI, eXch and OKX were already used as early as the second hop, after the initial dispersion.
Below is the full list of top interacted entities with >$100k inflows in the last 14 days (MEV is the default entity label for all MEV bots, irrespective of the operator). Note that this only tracks outflow volume and not net volume (e.g., Swapping stETH > ETH is counted as an outflow, and swapping this ETH > DAI will be counted as an outflow again, leading to a double amount of volume). Additionally, the 14 day threshold might also include transactions prior to the hack.
1. THORChain ($2,110,710,454.12 | WBTC, USDT, TGT, USDC, DAI, ETH)
First tx.: 2025-02-21 10:19:11 | Largest tx.: $2,815,131.38
2. ParaSwap ($412,840,619.63 | STETH)
First tx.: 2025-02-21 14:43:23 | Largest tx.: $68,634,931.90
3. Mantle ($348,374,602.23 | CMETH)
First tx.: 2025-02-21 15:25:35 | Largest tx.: $43,543,922.16
4. OKX DEX ($331,903,430.63 | ETH)
First tx.: 2025-02-13 11:06:11 | Largest tx.: $1,244,016.21
5. DODO ($84,721,918.52 | USDT, USDC, DAI, STETH)
First tx.: 2025-02-21 15:16:59 | Largest tx.: $41,696,473.25
6. Uniswap ($51,494,095.50 | WBTC, USDT, USDC, DAI, METH, ETH)
First tx.: 2025-02-15 03:34:47 | Largest tx.: $10,157,895.23
7. MEV ($50,206,485.81 | USDT, DAI, WBTC)
First tx.: 2025-02-22 02:34:35 | Largest tx.: $531,534.84
8. LI.FI ($27,175,974.67 | ETH)
First tx.: 2025-02-22 20:19:59 | Largest tx.: $80,528.51
9. eXch ($26,608,728.68 | USDC, DAI, ETH)
First tx.: 2025-02-22 09:32:11 | Largest tx.: $273,360.15
10. OKX ($16,941,056.59 | USDT, DAI, STETH)
First tx.: 2025-02-22 11:40:11 | Largest tx.: $1,221,168.98
11. Maya Protocol ($16,395,241.82 | ETH)
First tx.: 2025-02-20 17:55:11 | Largest tx.: $351,357.38
12. CoW Protocol ($9,540,793.13 | USDC, DAI, WBTC)
First tx.: 2025-02-22 13:44:23 | Largest tx.: $669,842.02
13. DLN ($7,831,071.40 | USDC, ETH)
First tx.: 2025-02-19 09:33:23 | Largest tx.: $1,086,376.86
14. SwftCoin ($4,622,223.87 | ETH)
First tx.: 2025-02-24 11:30:47 | Largest tx.: $87,247.63
15. Mimic Finance ($3,063,301.18 | DAI, ETH)
First tx.: 2025-02-23 08:37:59 | Largest tx.: $313,424.64
16. Across Protocol ($2,918,059.49 | ETH)
First tx.: 2025-02-24 08:52:11 | Largest tx.: $268,428.36
17. Bittorrent Chain ($2,789,566.22 | USDT, USDD, ETH)
First tx.: 2025-02-13 17:37:11 | Largest tx.: $191,757.38
18. Symbiosis ($550,066.91 | ETH)
First tx.: 2025-02-22 08:23:47 | Largest tx.: $34,224.66
19. Chainflip ($362,219.37 | USDC, ETH)
First tx.: 2025-02-22 07:04:35 | Largest tx.: $142,147.16
20. HitBTC ($345,268.77 | ETH)
First tx.: 2025-02-23 12:01:11 | Largest tx.: $36,402.34
21. MetaMask ($222,625.94 | DAI, ETH)
First tx.: 2025-02-23 10:17:23 | Largest tx.: $29,987.29
22. Tornado.cash ($112,794.42 | ETH)
First tx.: 2025-02-24 10:08:11 | Largest tx.: $26,842.84
Typical Lazarus Strategy
The process unfolded as follows:
- Liquidating the more illiquid assets: the stolen staked ETH tokens (such as stETH and mETH) were quickly swapped on decentralized exchanges for plain ETH, converting at least $200 million worth of staked tokens into ETH within hours (coindesk.com). This immediate dumping via DeFi was aimed at unstaking and consolidating value into Ethereum (which is more fungible and easier to move or convert further).
- Laundering phase: The Bybit hacker employed a maze of intermediary wallets and services to obfuscate the funds’ origin. The thieves moved the ETH through a web of addresses, token swaps, and cross-chain bridges, even using a no-KYC instant swap service to hop between networks. For example, the hacker attempts to channel large amounts of ETH through eXch (an Ethereum mixer protocol) and then bridges those funds to Bitcoin via the decentralized cross-chain swap platform.
These steps align with a typical Lazarus Group playbook: mix coins, change form (ETH to BTC or stablecoins), and spread them across chains to throw off trackers (chainalysis.com).
However, blockchain's transparency has allowed analysts to follow much of this activity in real time. In fact, as the hacker tried to use Chainflip, the protocol’s developers rushed to deploy an emergency update to block any wallets tied to the Bybit hack (cointelegraph.com).
Chainflip cut off its main interface to those addresses and upgraded its screening tools so that any deposit from the hacker’s wallets would be rejected and refunded instead of processed (cointelegraph.com). This was a notable instance of a decentralized protocol taking action to lock out a known thief. Similarly, other DeFi projects (and even oracle provider Chainlink) coordinated to ensure the hacker couldn’t easily exploit cross-chain services.
As of the end of February 2025, about 135,000 ETH (over $335 million) of the stolen haul has been successfully laundered or moved by the attacker, according to blockchain tracking reports. This implies roughly$900 million in ETH remains in the hacker’s wallets, still being gradually shuffled and monitored by investigators. The laundering is ongoing – one analyst noted the thief moved 45,900 ETH ($113M) in a 24-hour span on Feb. 26 alone. At the current dispersion rate, observers estimated it could take another week or two for the attacker to attempt to “clean” the rest if not stopped.
Mounting evidence strongly suggests that the notorious Lazarus Group of North Korea is behind the Bybit hack. Within hours of the breach, veteran on-chain sleuth ZachXBT investigated the hacker wallets and submitted “definitive proof” to analytics firm Arkham identifying Lazarus as the culprit (cryptobriefing.com).
This evidence included links between the Bybit exploit and previous Lazarus operations – notably, ZachXBT discovered that some of the same addresses were used in a $70 million Phemex exchange hack in January 2025. The stolen funds from Bybit were even found commingling with funds from the Phemex incident, strongly indicating a common actor (markets.businessinsider.com). Also the U.S. FBI officially attributed the $1.5B heist to North Korea, using the code-name “TraderTraitor” for the operation (reuters.com).
This public acknowledgement by law enforcement has galvanized a global investigative effort. Agencies like the FBI, Interpol, and others are now actively collaborating with Bybit and blockchain tracing experts to track the Lazarus Group’s crypto wallets, freeze any accessible assets, and ultimately hold the perpetrators accountable.
The Bybit hack of February 2025 stands as a stark reminder of the ingenuity and scale of modern cyber-heists targeting crypto platforms. A cunning supply-chain attack on a trusted wallet interface allowed state-sponsored hackers to steal an unprecedented sum, yet the incident also showcased the crypto industry’s resilience. Bybit’s decisive response – covering customer losses, fortifying systems, and rallying help from partners – helped contain the damage and reassure users.
Meanwhile, the transparent nature of blockchain enabled investigators to follow the money in real-time, and the united front presented by exchanges, law enforcement, and security firms has already led to frozen funds and critical intelligence. Though much of the stolen crypto is still in the wind, every passing day narrows the hackers’ options for laundering. The Bybit case will likely drive new security innovations (such as better transaction verification and multisig safeguards) and stronger inter-exchange cooperation. Ultimately, this record-breaking hack underlines the ongoing threats in the crypto space and the importance of swift, collaborative responses to protect the ecosystem’s integrity.

